


Linux offers a robust set of command line tools that prove invaluable in digital investigations. Among these command tools, the ‘file’ command line stands out. It enables the identification of a file’s type based on its content, making it particularly useful when file extensions have been altered.
Take, for example, the screenshot below, showcasing a file named ‘fun.doc’. Although the file extension suggests it is a Word Document, the ‘file’ command allows us to verify its true type based on its content.
Now we will use ‘file’ command to find out the exact type of the file:
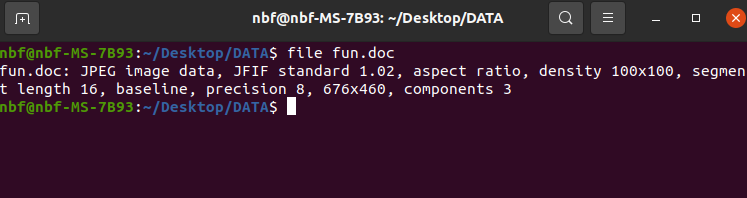
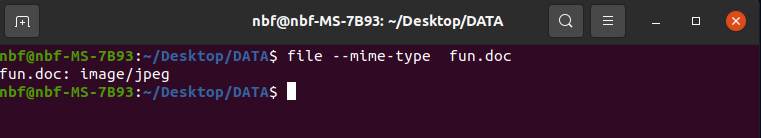
Upon examining the screenshot above, it becomes evident that the file named “fun.doc” is not, in fact, a Word document as initially presumed. Instead, it appears to be a JPEG file, highlighting the importance of verifying file types beyond their given extensions.
To reinforce our findings, we can employ the ‘hexdump’ command line tool to inspect the file’s signature. By analyzing the hexadecimal representation of the file’s content, we can obtain a more definitive confirmation of its true format.
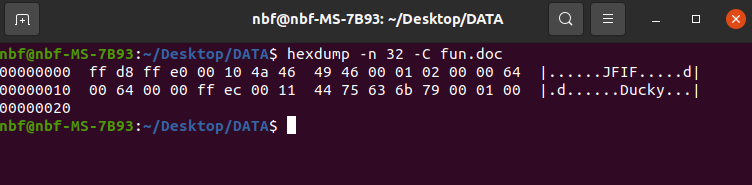
The output of the ‘hexdump’ command reveals the file header, indicating that the examined file possesses the characteristic header of a ‘JPEG’ file format (FF D8 FF).
These powerful Linux command line tools serve as indispensable assets, empowering us to enhance our digital forensics capabilities. By leveraging the capabilities of these tools, we can acquire deeper insights into file analysis, uncover hidden information, and bolster our proficiency in the field of digital forensics.